Empower every engineer to own the security of their code
Full code-to-cloud security coverage in minutes with Security Plans
Replace siloed application and cloud security tools with a unified solution that makes many tools feel like one.






Review

Scanner

Review

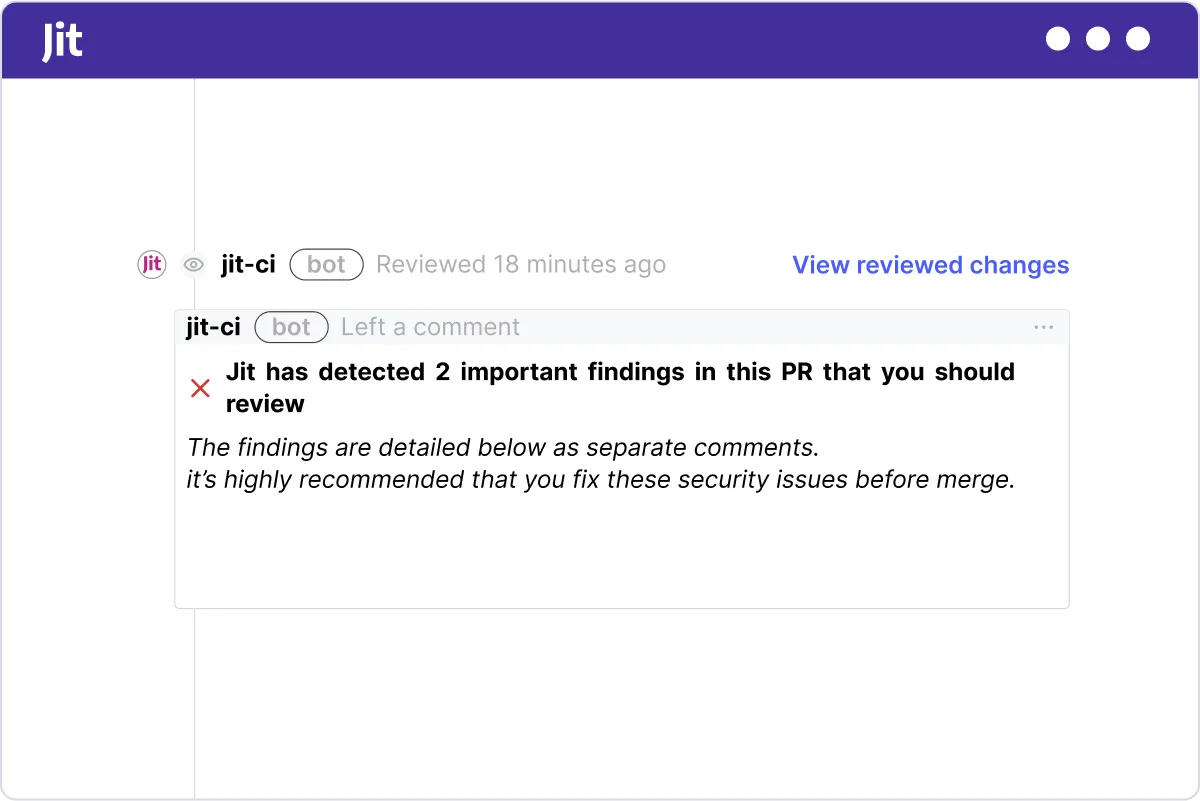
Immediate feedback for developers on the security of every code change
Jit’s unique iterative scanning only returns issues related to the current code change — accelerating scan times while preventing vulnerability overload.
Automatically prioritize your product security risks, while minimizing false positives
Solve security issues quickly with automated code suggestions, thorough vulnerability descriptions, and bulk remediations.
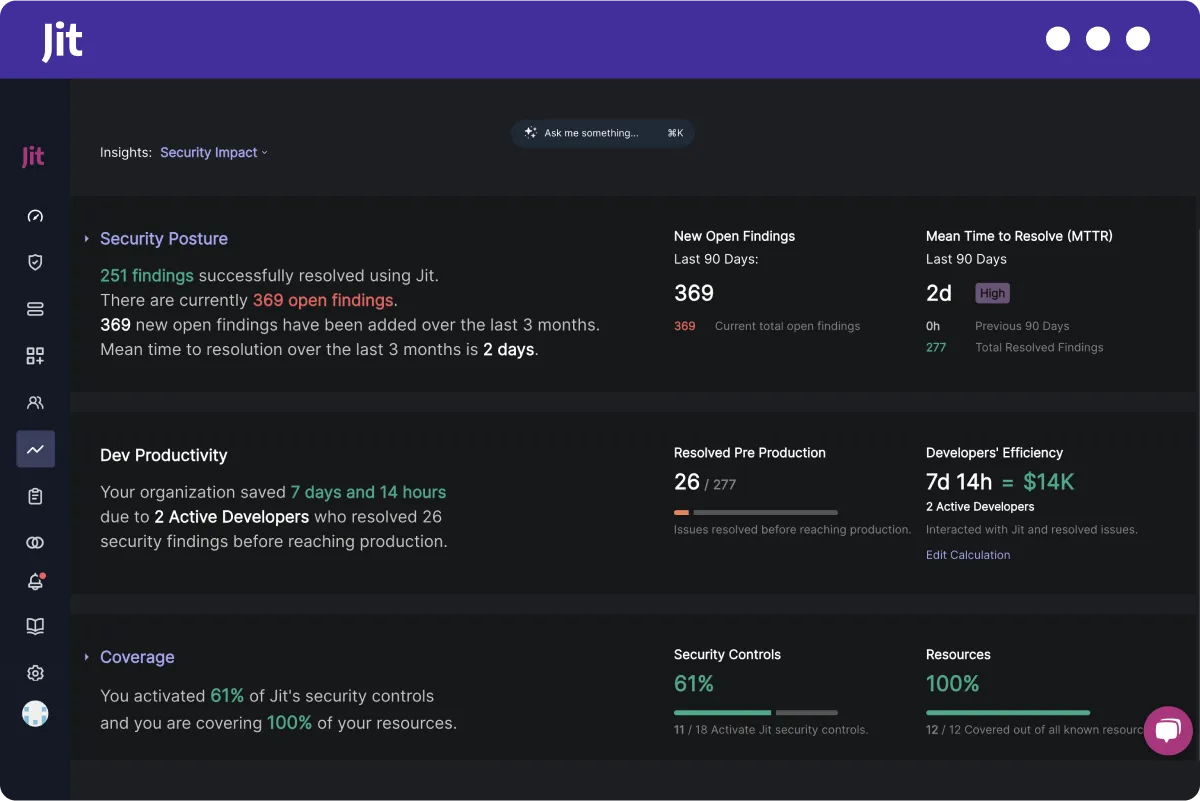
Measure security posture per team, while gamifying security for developers
Promote a proactive security engineering culture by enabling every team to monitor their security score, based on open vulnerabilities.
Integrate any tool into Jit’s extensible orchestration framework
Detection

Semgrep provides lightweight static analysis security testing (SAST) for many languages. Compare Semgrep SAST results with other popular SAST tools. Jit adds our own rules to Semgrep to cover additional findings.


Use Gitleaks to surface hard-coded secrets that can be exploited by attackers to gain unauthorized access to the password-protected asset.


Use OSV-Scanner (by Google) to find existing vulnerabilities affecting your project’s dependencies. The tool uses the data provided by https://osv.dev. Support Python and PHP.


Use Trivy (by Aqua Security) to scan for vulnerabilities in container images, file systems, and Git repositories, as well as for configuration issues.


The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by a dedicated international team of volunteers. Use ZAP to run dynamic tests against web apps and APIs to surface a huge list of vulnerabilities.


Find security vulnerabilities, compliance issues, and infrastructure misconfigurations early in the development cycle of your infrastructure-as-code with KICS by Checkmarx.


Prowler is an spen source tool to perform AWS security best practices assessments, audits, continuous monitoring, hardening and forensics readiness. It contains more than 200 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.


Legitify makes it east to detect and remediate misconfigurations and security risks across all your GitHub and GitLab assets.


Use Trufflehog to surface hard-coded secrets that can be exploited by attackers to gain unauthorized access to the password-protected asset. Trufflehog can determine whether an hard-coded secret will be exposed in production.


Surface known vulnerabilities in open source components written in Javascript or Typescript. NPM-audit is powered by the GitHub Advisory Database.


Kubescape (by Armo) provides vulnerability and misconfiguration scanning for IaC files being deployed to Kubernetes.

Jit has you covered
Languages
Vulnerabilities
Dev Environment
Stay in the Know